Healtys©
Healtys is a comprehensive healthcare app designed to support a healthier future. It offers an all-in-one service, from booking doctor appointments to securely viewing and digitally signing medical procedures.
Scope
Background
As a healthcare app, Healtys is committed to safeguarding users’ personal medical data, ensuring that only the user and their trusted representatives can access or grant permission to it. Given that medical conditions often require immediate action, the process must be both seamless and secure. Our goal is to elevate this experience by designing a flow that prioritizes clarity, security, and ease of use while making users feel confident and not intimidated.
The challenges
Apps that require personal data often face trust challenges, which can slow down the verification process. The key challenges are :
1. Building sufficient trust for users to willingly complete verification.
2 Managing trusted individuals to view information or perform actions.
Business goals
Stakeholders want this feature implemented to prevent fraud and strengthen security, while also ensuring users feel comfortable with the additional verification step and fostering greater trust.
Problem solving process
We start by defining business goals and breaking them into actionable parts to guide relevant design patterns. which is :
1. Enhance Security
2. Ensure Comfort
3. Building Trust
Building on these three key principles, we continued our work with secondary research through Competitor and Benchmark Analysis. This approach helps us avoid reinventing the wheel while identifying industry best practices.
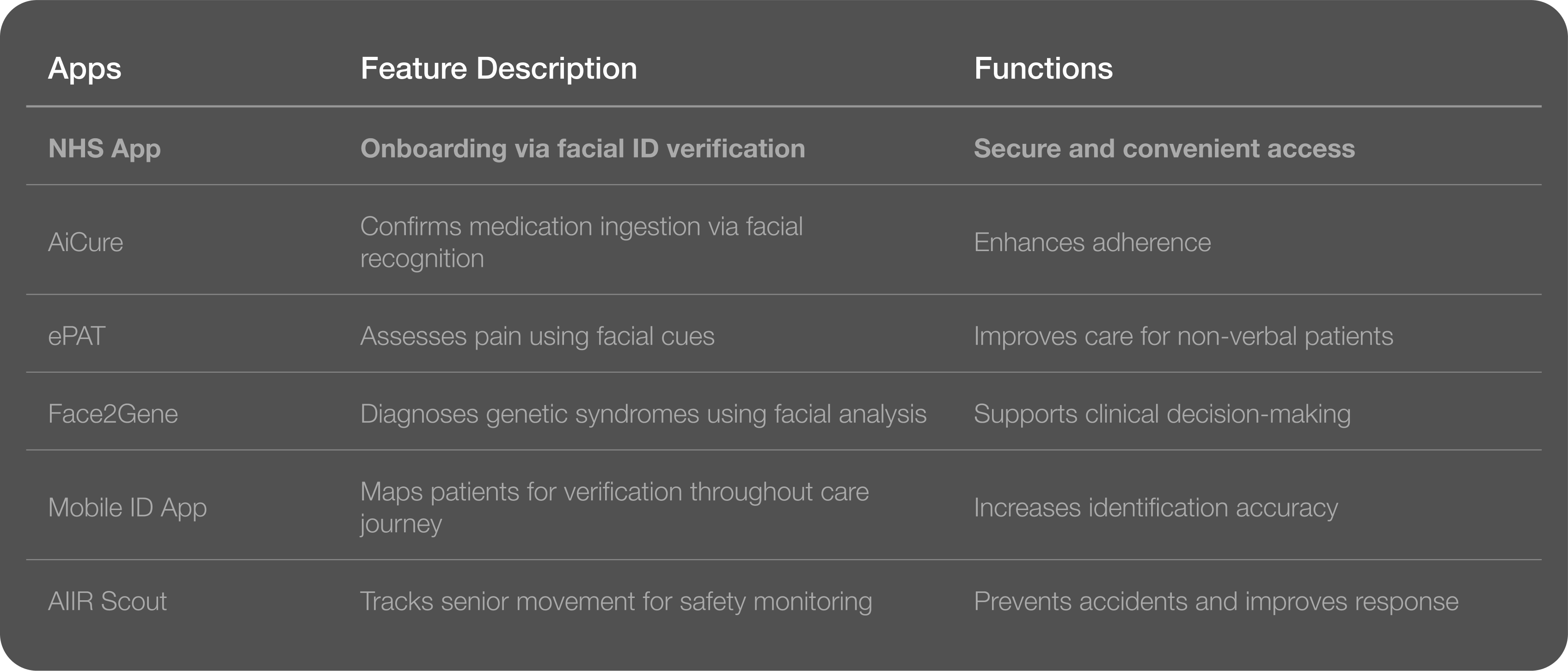

Our research shows that while many apps utilize facial detection for different functions, the NHS App presents the closest use case to our intended purpose.

The Solution
We integrated our pattern findings with established theoretical frameworks to inform and support the solutions we aim to achieve.
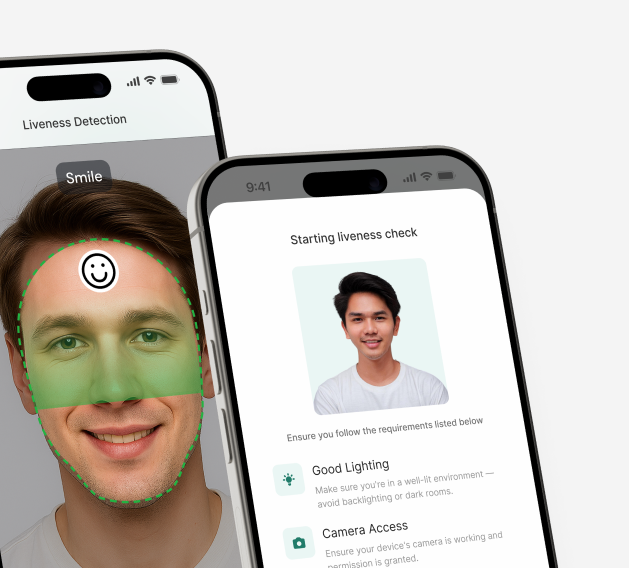
Ensure users feel secure and confident throughout the verification process.
This can be achieved by applying the Trust in Technology models (Mayer, Davis, & Schoorman, 1995; McKnight et al., 2002), which highlight competence, integrity, and benevolence as key factors in building user trust in digital systems. To support this, the use of clear microcopy, visible trust signals (such as lock icons, GDPR notices, and reassurance messages like ‘your data is safe’), and transparent onboarding is essential. In addition, Universal Design and Inclusive Design theories emphasize the importance of creating systems that are accessible across different abilities, languages, and levels of digital literacy. Drawing from these principles, onboarding should be designed to ensure that both digital natives and less tech-savvy users can navigate the process with ease and confidence.
Implementation

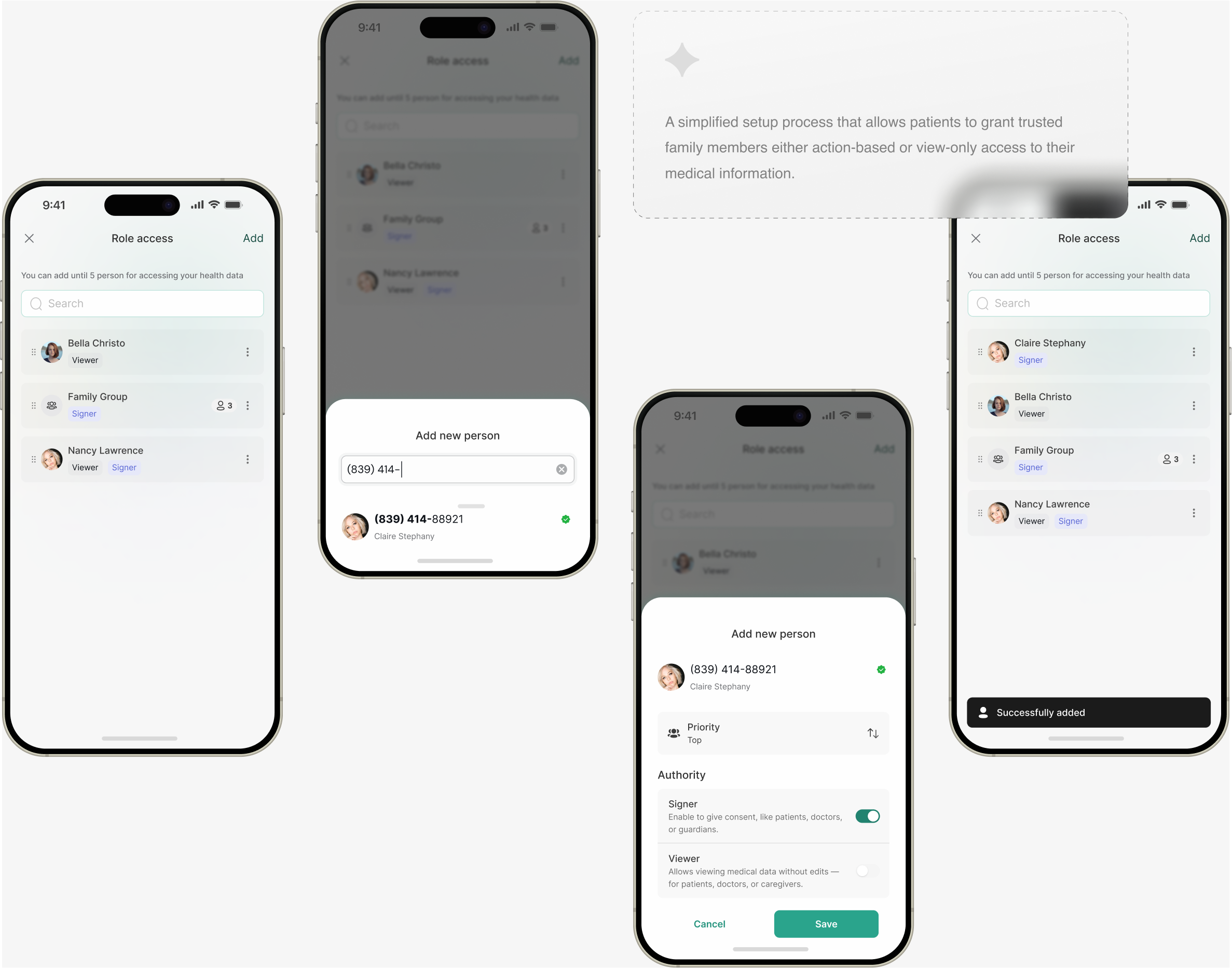
Managing trusted individuals to view information or perform actions
This can be achieved by grounding the design in several theoretical foundations. Information Architecture and Cognitive Load Theory (Sweller, 1988) emphasize the clear separation of roles (viewer, signer) to minimize cognitive overload by showing users only the actions relevant to them. Social Roles Theory (Biddle, 1986) highlights the value of translating familiar real-world roles into digital systems (e.g., family groups, medical proxies), making interactions more intuitive and trustworthy. Furthermore, Nielsen’s Usability Heuristics (1994) underscore the importance of ‘user control and freedom,’ enabling users to confidently manage access, and ‘visibility of system status,’ which ensures role capabilities are clearly communicated to prevent errors.
Implementation